

Penetration Testing & Vulnerability Scanning
Guardian 365 Pen Testing services are designed to test vulnerabilities and weaknesses within computer systems and applications by simulating a cyber attack on a computer system, network, or web application. Schedule your penetration test to uncover new defects and test the security of communication channels and integrations.
Pen Testing & Vulnerability Scanning.
Minor changes to your system can create new untapped exposures that must be quickly identified and patched.
Hackers are working around the clock using advanced automation to attack your environment. Guardian 365 Pen Testing works to identify IP addresses and web applications for testing, execute pen tests and vulnerability scans, and devise a coverage plan. But how?
Annual Penetration Testing.
Guardian 365 includes Annual Pen Testing that focuses on three key areas of interest to insurance companies:
We identify hazardous configuration issues and vulnerabilities that can be exploited by external and internal attackers to gain unauthorized access to your systems and to test web applications for any weaknesses or technical flaws.
Attack Surface Assessments.
Identify the infrastructure vulnerabilities putting your organization at risk before it’s too late.
Prioritized risk assessments provide verified critical security vulnerabilities that evaluate infrastructure gaps and monitor web applications. This ensures that any new vulnerabilities are identified and addressed before they can be exploited by bad actors.
Documentation, Reporting & Review.
Understanding your vulnerabilities and how to address key areas of concern is critical for your future planning and security management.
You’ll get documented reports, strategic recommendations, and scan reviews of your system to remediate identified issues. We work with you to ensure you have identified threats and successful patching of gaps.
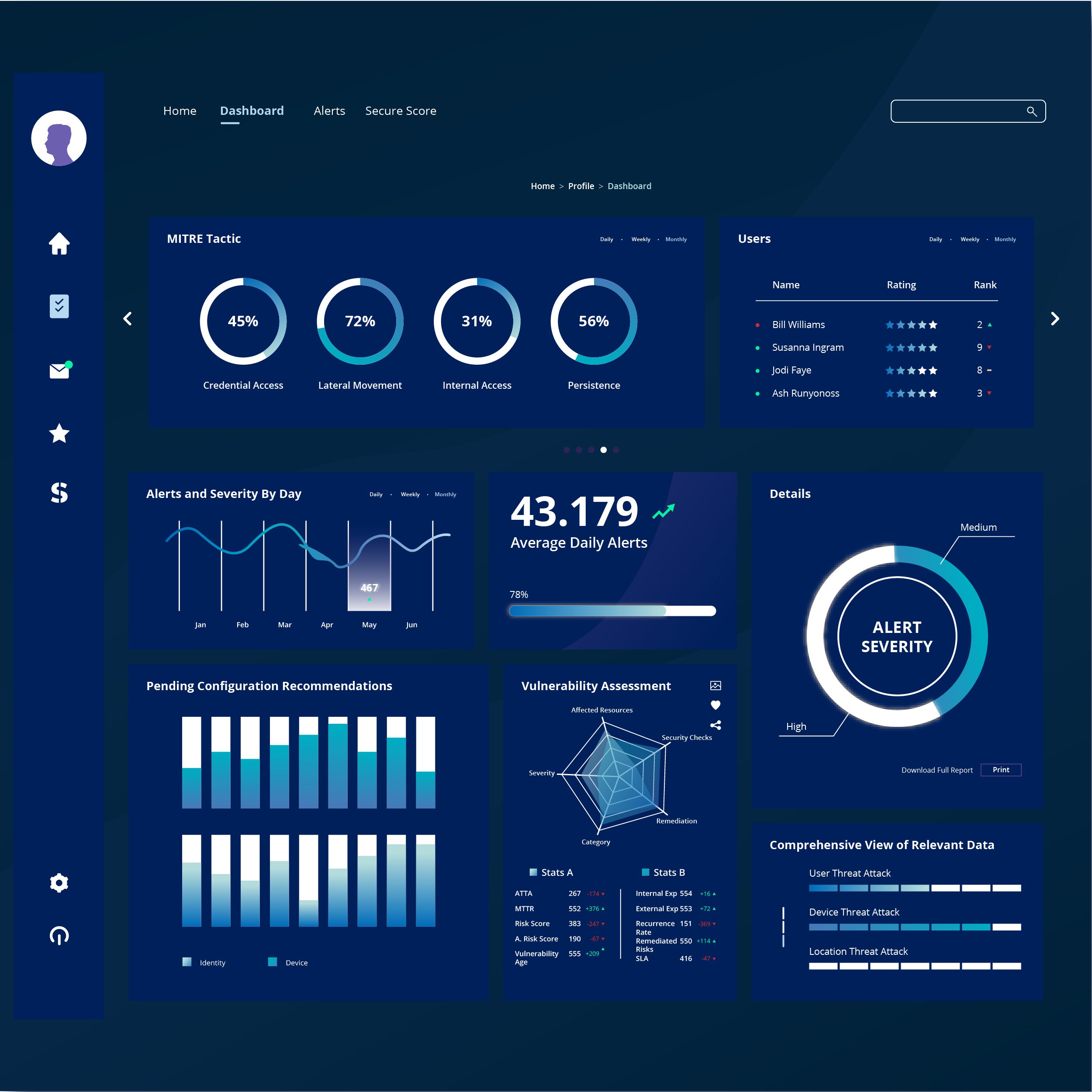
Stay Steps Ahead.
Don’t wait for a successful cyberattack to identify the gaps and vulnerabilities in your security posture.
Partner with Guardian 365 to take advantage of the active threat assessment and strategic response that Guardian 365 can deliver for your organization. We’ll support your organization’s progress toward robust and reliable responses that can give you complete confidence in your collaborative environments.
Mastering Credential Management: A Cornerstone of Modern Cybersecurity In an era where digital threats are
Enhancing Email Security: Fine-tuning Microsoft Defender for Office with Guardian 365 In the dynamic landscape
Maximize Your Microsoft A5 Security Investment Please note, while there are a few differences between
Empowering Small IT Teams with Big Security Superpowers Learn how Forsyte works with Guardian 365
PRIORITIZING SECURITY FOR THE CCC SYSTEMIn 2023, the California Community College Chancellor's Office (CCCCO) supported



You’re in the right place! Complete the form to hear the latest Guardian 365 security discussion featuring IT leaders from Spelman College and Spring Grove Area School District. You won’t want to miss this!

Let us help you save money on your Cybersecurity Insurance by providing an audit of your current environment, and provide recommendations on how to reduce the cost of your insurance policy,

At Forsyte Guardian 365, we believe in transparency and hands-on experiences. Complete the form to request your personalized demo. Remember, security is not a luxury. It’s a necessity. Let’s empower your team with Guardian 365!


If you are experiencing a security breach or have detected suspicious activity, get help now.

If you are experiencing a security breach or have detected suspicious activity, get help now.