robust security for all industries
Protecting organizations across industries, regardless of size.
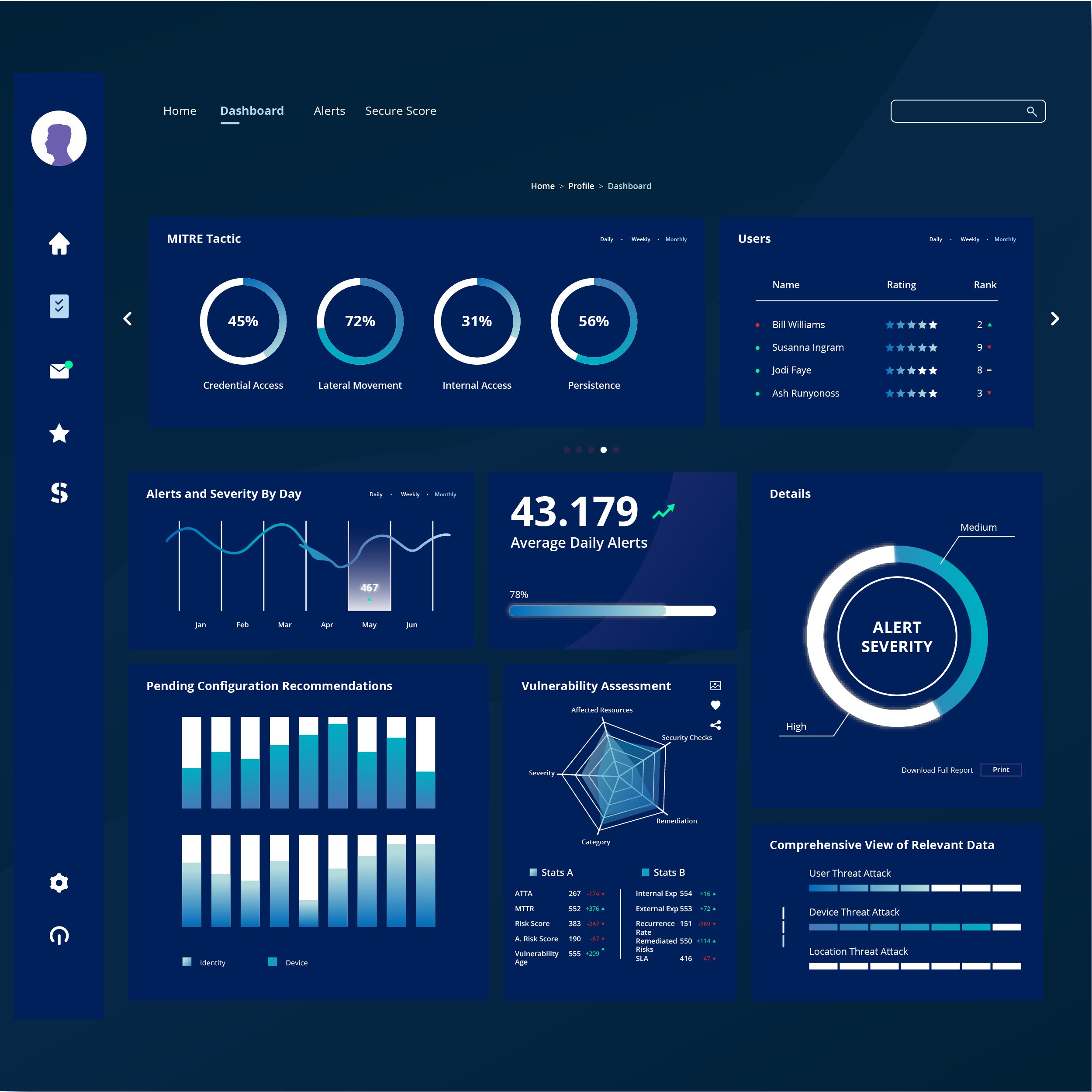
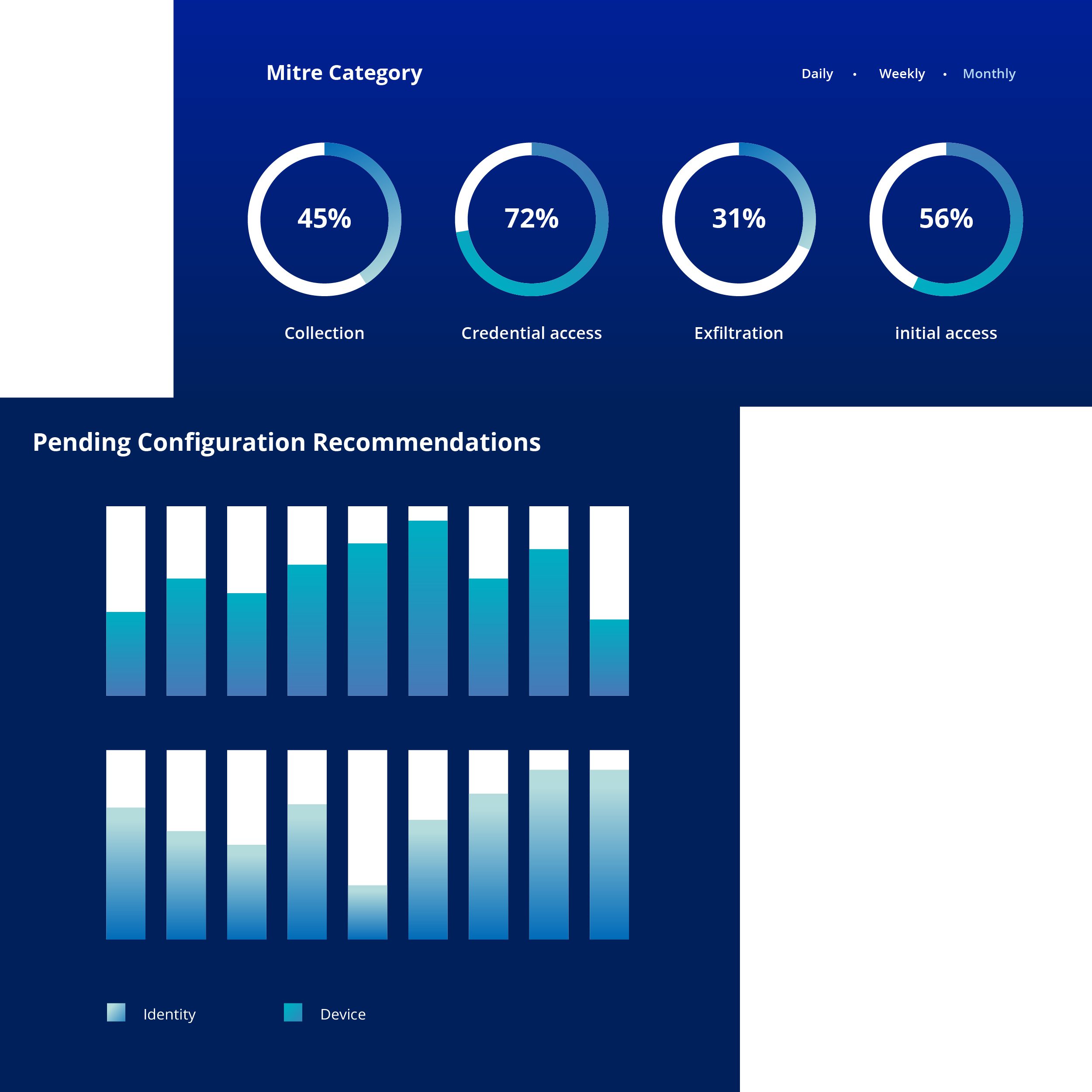
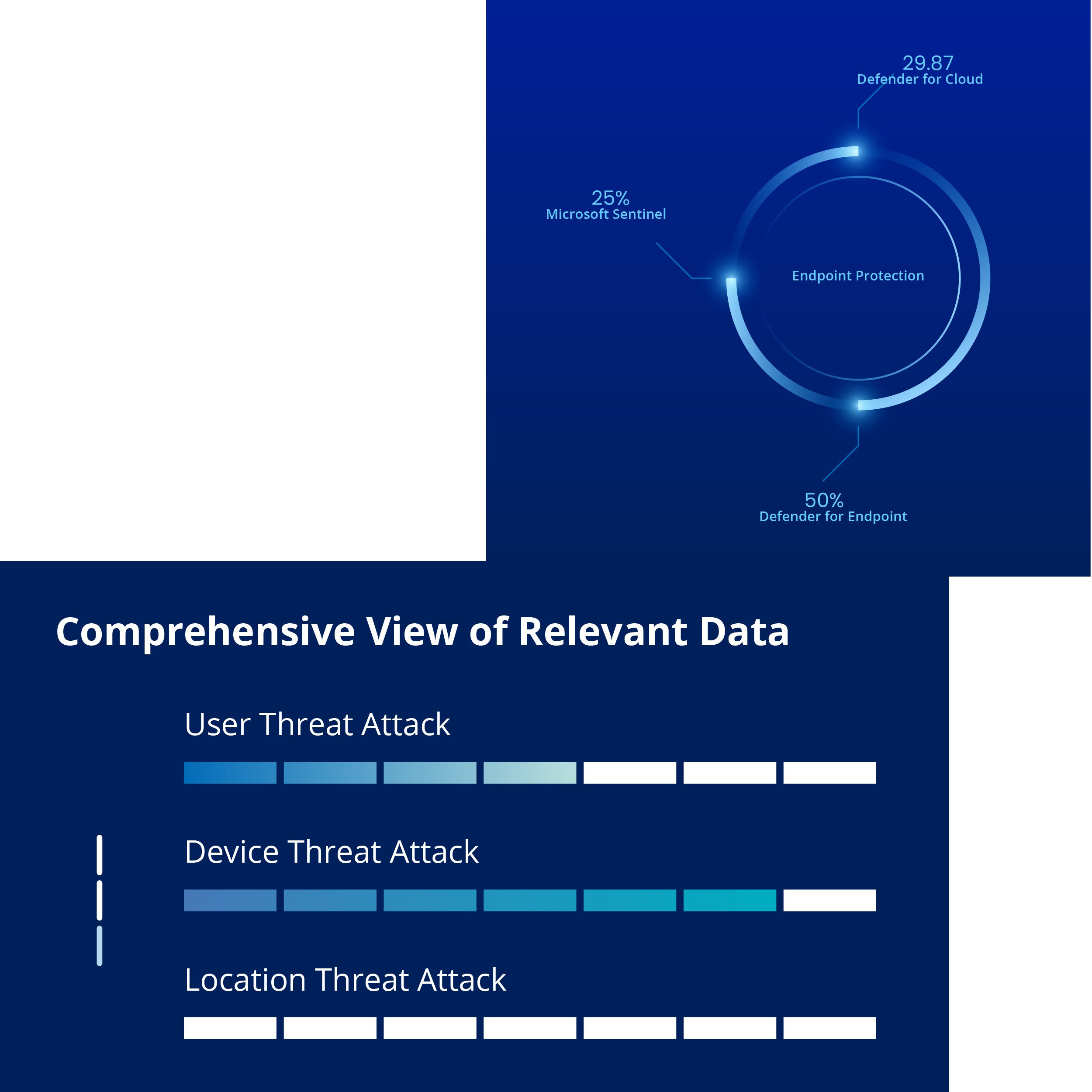
Guardian 365 ensures robust security for organizations of all sizes and diverse industries. Whether you're a small startup, a mid-sized enterprise, or a large corporation, we make it easy to secure Guardian 365 managed security.
Guardian 365 is customized for every client, ensuring the unique needs of Higher Education, K12 Education, Government, Commercial, and other sectors are met, no matter how stringent they are.